Security in layman’s terms
Anant was browsing the internet when he came across an advertisement for an 80% off branded dress. Anant became enthralled and clicked on the link. He double-checked the dress and its size. He found it to be a good fit and added it to his cart. He then made the payment by entering his credit card information. He was excited because he had obtained a good dress at a significant discount, which he intended to purchase for his friend’s wedding. After a few minutes, he received an alert that a transaction from his card had been processed, which he had not done. He was taken a back and had no idea what was going on. When he checked the same website again, he found that it is an unsecured website. His card information was stolen, but he was able to block his card after being notified of the fraudulent transaction.
Why Security is important for IoT products
Anant realised that the same thing could happen at his plant, where multiple IoT devices spread across different units of the plant are connected over the internet, sending machine statistics, plant operational details such as production rate, machine health, and a variety of other information. Some Internet of Things devices could indeed control plant machinery. Certainly, the IoT devices have greatly helped him in maintaining uptime, increasing productivity, and identifying faults in real time so he can’t ignore them. To make matters worse, there was no way for him to determine whether any of the systems had already been hacked or compromised, as he could with his credit card.
He was now convinced that data security is extremely important for any remote monitoring or control system he deploys at his plant.
How security can be achieved in the Internet of Things world?
Anant requested the assistance of his IT team to assess data security options. His IT team informed him that there are very few suppliers who provide end-to-end security. End-to-end security means that before an IoT device sends data to a server, it first authenticates the server to ensure that it is communicating with the correct server. The server does the same thing before allowing any IoT device to connect to itself. After both the IoT device and the server have authenticated each other, they can begin exchanging information or data. Again, data cannot be plain data in order for unknown parties or hackers to interpret the information. So the IoT device encrypts the data before sending it to the server, and the server does the same. Data encryption ensures that the recipient does not understand what was communicated between the two ends.
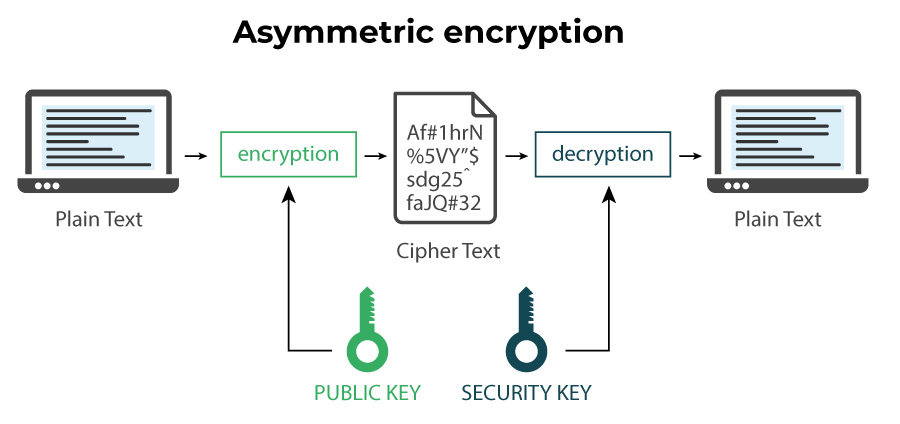
How iEdge 360 accomplishes this in a very intuitive and user-friendly manner
At CIMCON Digital, data security is as important as meeting business requirements. However, data security is a complex topic that requires in-depth knowledge, sometimes even at the end-user level. This is also why end users skip the security step unless IT or management enforces it. Fortunately, it is simple and straightforward for iEdge360 users. CIMCON Digital’s iEgde360 is an IoT Edge gateway platform.
Initially, iEdg360 employs industry-standard security practices, so users do not need to learn anything new, and the credibility of those security standards is already established. iEdg360, for example, uses an X.509 certificate-based MQTT connection with the server. The International Telecommunication Union (ITU) standard X.509 specifies the format of public key certificates. X.509 certificates are used in many Internet protocols, including TLS/SSL, which serves as the foundation for HTTPS, the secure web browsing protocol.
Second, the user simply selects that they want to connect the field device using secured MQTT, and the platform will generate the necessary X.509-based certificates and upload the public key to the endpoint (server). As a result, the end user does not need to worry about creating certificates or uploading keys to the server. The process is so seamless that the end user may not even be aware of this technology and still achieve end-to-end security.
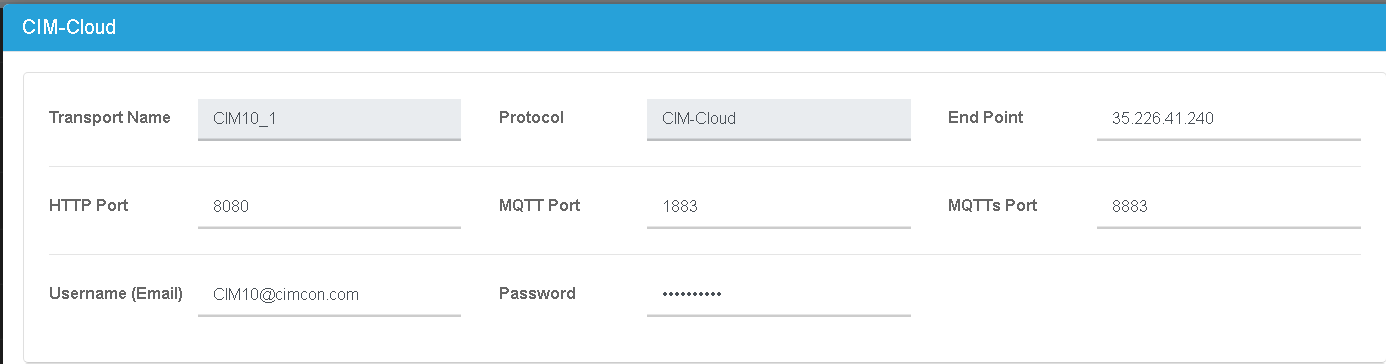
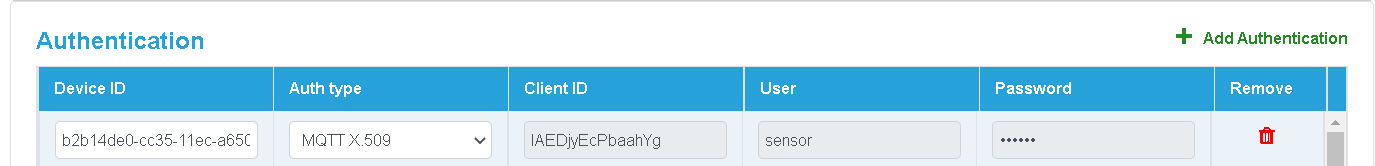
iEdge360 MQTT configuration
Why are CIM devices safe to use?
CIM, an IoT Edge gateway from CIMCON Digital, is part of the iEdge360 platform. CIM includes data security out of the box, allowing end users to protect plant and machine data. Only an authorized user can view the data once it has arrived at the server by entering user credentials. CIMCON Digital’s cloud solution, CIM-Cloud, which displays data in a dashboard and performs analytics, also uses two-factor authentication (2FA). Two-factor authentication improves security. After providing valid login credentials, the user is prompted for an authentication code, which is sent to his email address. As a result, even if user credentials are stolen, an anonymous person cannot log in. This function is available in the majority of financial portals but not in IIoT platforms. CIMCON Digital is one of the few platform companies that has implemented Two Factor Authentication(2FA).
Summary
Data security is critical for protecting plant and machine data while implementing Digital Transformation in factories. Because implementing data security is difficult and too technical for end users, it is often avoided, and people deploy unsecured IoT devices and gateways. Data security can now be easily implemented with CIMCON Digital’s IoT Edge Gateway and CIM-Cloud, so users no longer need to worry about technology and can have peace of mind knowing that all operational data is in safe hands.


